The following are textbook/encyclopedic definitions of some key concepts to Anti_Illuminati's work. This following post is just the basic background of these concepts. Anti_Illuminati shows the vulnerabilities and "back doors" to these following systems in his research. For now, we will just look at their "cover stories"
Revolution in Military Affairs The military concept of Revolution in Military Affairs (RMA) is a theory about the future of warfare, often connected to technological and organizational recommendations for change in the United States military and others.
Especially tied to modern information, communications, and space technology, RMA is often linked to current discussions under the label of
Transformation and total systems integration in the US military.
RMA is defined by RAND as a:
a military technical revolution combining [technical advances in] surveillance, C3I [command, control, communications, and intelligence]
and precision munitions [with new] operational concepts, including information warfare, continuous and rapid joint operations
(faster than the adversary), and holding the entire theater at risk (i.e., no sanctuary for the enemy, even deep in his own battlespace)
RAND has a brief 14 page summary of RMA here:
http://www.rand.org/pubs/monograph_reports/MR1029/MR1029.chap2.pdf

Command and control, or C2, in a military organization can be defined as the exercise of authority and direction by a properly designated commanding officer over assigned and attached forces in the accomplishment of the mission.
Command and control functions are performed through an arrangement of personnel, equipment, communications, facilities, and procedures employed by a commander in planning, directing, coordinating, and controlling forces and operations in the accomplishment of the mission.
Commanding officers are assisted in executing these tasks by specialized staff officers and enlisted personnel. These military staff are a group of officers and enlisted personnel that provides a bi-directional flow of information between a commanding officer and subordinate military units.
The purpose of a military staff is mainly that of providing accurate, timely information which by category represents information on which command decisions are based. The key application is that of decisions that effectively manage unit resources. While information flow toward the commander is a priority, information that is useful or contingent in nature is communicated to lower staffs and units.
In military usage, a number of abbreviations in the format C(x) followed by additional letters are used, based on expanded versions of the abbreviation C2 - command and control.
* C²/C2/C&C (Command and control)
* C²IS (command and control information systems)
* C³ (command, control, and communications) [US DoD]
* C3 (consultation, command, and control) [NATO]
* C³I (command, control, communications, and intelligence)
* C4 (command, control, communications, and computers)
* C4IS (command, control, communication, computer, and intelligence simulator system)
*
C4ISR (command, control, communications, computers, intelligence, surveillance, and reconnaissance)
* C4I (command, control, communications, computers, and intelligence)
* C4I² (command, control, communications, computers, intelligence, and interoperability)
* C5I (command, control, communications, computers, combat systems, and intelligence)
* C5ISR (command, control, communications, computers, combat systems, intelligence, surveillance, and reconnaissance)
The most common formats that Anti_Illuminati covers in his research are C2, C³, and especially
C4ISR.
Lookup
C4ISR in a search engine.
Situation awareness, situational awareness, or SA, is the perception of environmental elements within a volume of time and space, the comprehension of their meaning, and the projection of their status in the near future. It is also a field of study concerned with perception of the environment critical to decision-makers in complex, dynamic areas from aviation, air traffic control, power plant operations, military command and control, and emergency services such as fire fighting and policing; to more ordinary but nevertheless complex tasks such as driving an automobile or motorcycle.
Situation awareness (SA) involves being aware of what is happening around you to understand how information, events, and your own actions will impact your goals and objectives, both now and in the near future. Lacking SA or having inadequate SA has been identified as one of the primary factors in accidents attributed to human error. Thus, SA is especially important in work domains where the information flow can be quite high and poor decisions may lead to serious consequences (e.g., piloting an airplane, functioning as a soldier, or treating critically ill or injured patients).
Having complete, accurate and up-to-the-minute SA is essential where technological and situational complexity on the human decision-maker are a concern. SA has been recognized as a critical, yet often elusive, foundation for successful decision-making across a broad range of complex and dynamic systems, including aviation and air traffic control, emergency response and military command and control operations, and offshore oil and nuclear power plant management.
Although numerous definitions of SA have been proposed, Endsley's definition (1995b), "the perception of elements in the environment within a volume of time and space, the comprehension of their meaning, and the projection of their status in the near future," is firmly established and widely accepted. While some definitions are specific to the environment from which they were adapted, Endsley's definition is applicable across multiple task domains. Several other definitions of SA have been suggested, generally restating the same themes:
* "accessibility of a comprehensive and coherent situation representation which is continuously being updated in accordance with the results of recurrent situation assessments" (Sarter & Woods, 1991)
* "the combining of new information with existing knowledge in working memory and the development of a composite picture of the situation along with projections of future status and subsequent decisions as to appropriate courses of action to take" (Fracker, 1991b)
* "the continuous extraction of environmental information along with integration of this information with previous knowledge to form a coherent mental picture, and the end use of that mental picture in directing further perception and anticipating future need" (Dominguez, Vidulich, Vogel, & McMillan, 1994)
* "adaptive, externally-directed consciousness that has as its products knowledge about a dynamic task environment and directed action within that environment" (Smith & Hancock, 1995)
* "the ability to maintain a constant, clear mental picture of relevant information and the tactical situation including friendly and threat situations as well as terrain" (Dostal, 2007)
* SA is simply "knowing what is going on so you can figure out what to do" (Adam, 1993)
* "what you need to know not to be surprised" (Jeannot, Kelly, & Thompson, 2003)
* The term SA "is a shorthand description for "keeping track of what is going on around you in a complex, dynamic environment" (Moray, 2005, p. 4)
* The "aim of efficient SA is to keep the operator tightly coupled to the dynamics of the environment"
Before being widely adopted by human factors scientists in the 1990s, the term was first used by United States Air Force (USAF) fighter aircrew returning from war in Korea and Vietnam. They identified having good SA as the decisive factor in air-to-air combat engagements—the "ace factor".
Survival in a dogfight was typically a matter of observing the opponent's current move and anticipating his next move a fraction of a second before he could observe and anticipate his own. USAF pilots also came to equate SA with the "observe" and "orient" phases of the famous observe-orient-decide-act loop (OODA Loop) or Boyd cycle, as described by the USAF fighter ace and war theorist Col. John Boyd. In combat, the winning strategy is to "get inside" your opponent's OODA loop, not just by making your own decisions quicker, but also by having better SA than the opponent, and even changing the situation in ways that the opponent cannot monitor or even comprehend. Losing one's own SA, in contrast, equates to being "out of the loop."Read more about "situational awareness" here:
http://en.wikipedia.org/wiki/Situation_awarenessAnd look it up on a search engine to read Military and Government white papers on the subject.
 The Global Information Grid (GIG)
The Global Information Grid (GIG) is an all-encompassing communications project of the United States Department of Defense. It is defined as a "globally interconnected, end-to-end set of information capabilities for collecting, processing, storing, disseminating, and managing information on demand to warfighters (soldiers), policy makers, and support personnel."
The GIG includes owned and leased communications and computing systems and services, software (including applications), data, security services, other associated services, and National Security Systems.
Non-GIG IT includes stand-alone, self contained, or embedded IT that is not, and will not be, connected to the enterprise network. (off the grid)The GIG is managed by a construct known as NetOps. NetOps is defined as the operational framework consisting of three essential tasks, Situational Awareness (SA), and Command & Control (C2) that the Commander (CDR) of US Strategic Command (USSTRATCOM), in coordination with DoD and Global NetOps Community, employs to operate and defend the GIG to ensure information superiority.
Search
Global Information Grid in a search engine.
Watch this 20 minute entertaining "music video"/documentary on the Global Information Grid.
DARPA IXO
http://www.veoh.com/browse/videos/category/news/watch/v18575342wGfPZSA8

NETWORK-CENTRIC / NET-CENTRIC
Netcentric, or "network-centric", refers to participating as a part of a continuously-evolving, complex community of people, devices, information and services
interconnected by a communications network to optimize resource management and provide superior information on events and conditions needed to empower decision makers.
The network itself is only one of several enabling factors along with sensors, data processing and storage, expert analysis systems and intelligent agents, and information distribution. The largest commercial practitioners of globally distributed supply chain management and customer relationship management employ net-centric methods.
Network Centric Product Support (NCPS) is a specific example of the netcentric architecture that is being applied to a range of applications including the NextGen airtraffic control as well as other transportation applications.
Netcentric warfare is also a tenet of modern information warfare concepts. A Net-centric Enterprise Architecture is defined in lay terms as a: "massively distributed architecture with components and/or services available across and throughout an enterprise's entire lines-of-business."
The formal definition of a "NetCentric Enterprise Architecture" is: "A NetCentric Enterprise Architecture is a light-weight, massively distributed, horizontally-applied architecture, that distributes components and/or services across an enterprise's information value chain using Internet Technologies and other
Network Protocols as the principal mechanism for supporting the distribution and processing of information services."
Look up
Network Centric Warfare in a search engine
Look up
netcentric in a search engine
 Enterprise architecture
Enterprise architecture is a comprehensive framework used to manage and align an organization's Information Technology (IT) assets, people, operations, and projects with its operational characteristics. In other words, the enterprise architecture defines how information and technology will support the business operations and provide benefit for the business.
It illustrates the organization’s core mission, each component critical to performing that mission, and how each of these components is interrelated. These components include:
* Guiding principles
* Organization structure
* Business processes
* People or stakeholders
* Applications, data, and infrastructure
* Technologies upon which networks, applications and systems are built
Guiding principles, organization structure, business processes, and people don’t sound very technical. That’s because enterprise architecture is about more than technology. It is about the entire organization (or enterprise) and identifying all of the bits and pieces that make the organization work.
Enterprise Architecture’s Benefits
A well-documented, well-understood enterprise architecture enables the organization to respond quickly to changes in the environment in which the organization operates. It serves as a ready reference that enables the organization to assess the impact of the changes on each of the enterprise architecture components. It also ensures the components continue to operate smoothly through the changes.
An Analogy to City Planning
You can relate enterprise architecture to the more widely understood concept of city planning. In city planning, zones are established for very specific purposes. The buildings that are built in these zones are constructed to specifications to meet those purposes.
For example, a hospital is built to different specifications than a house or office building. Additionally, to ensure uniformity of the city and to ensure roads link to each other and pipes attach to each other without a problem, city planners establish specific guidelines on building materials and interface specifications.
In the case of enterprise architecture, the enterprise is analogous to the city. The organization structure represents the zones established to execute the enterprise’s core mission. Buildings are analogous to applications and systems. Likewise, technical elements, such as infrastructure hardware, design specifications, and development languages, are analogous to building materials and interface specifications and are used to implement the applications and systems.
The following table depicts these analogous relationships:
City Plan is to . . . as enterprise architecture is to . . .
1. zones 1. organization structure
2. buildings 2. applications and systems
3. building materials 3. infrastructure hardware, design specifications, and development languages.
and interface specifications
Source:
http://enterprisearchitecture.nih.gov/About/What/Anti_Illuminati's video
Ptech Built Supply Chain Infrastructure - Destruction of Free Market has very good illustrations of Enterprise Architecture done by Unisys:
Watch it here about an hour long:
Search
Enterprise Architecture in a Search Engine
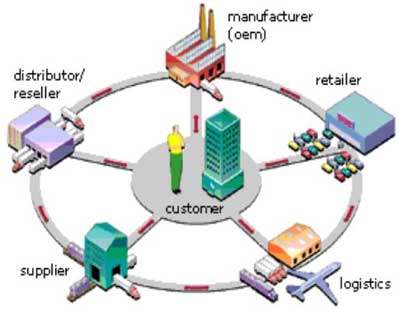 Supply ChainA supply chain is a system of organizations, people, technology, activities, information and resources involved in moving a product or service from supplier to customer. Supply chain activities transform natural resources, raw materials and components into a finished product that is delivered to the end customer.Supply chain management
Supply ChainA supply chain is a system of organizations, people, technology, activities, information and resources involved in moving a product or service from supplier to customer. Supply chain activities transform natural resources, raw materials and components into a finished product that is delivered to the end customer.Supply chain managementThe primary objective of supply chain management is to fulfill customer demands through the most efficient use of resources, including distribution capacity, inventory and labor. In theory, a supply chain seeks to match demand with supply and do so with the minimal inventory. Various aspects of optimizing the supply chain include liaising with suppliers to eliminate bottlenecks; sourcing strategically to strike a balance between lowest material cost and transportation, implementing JIT (Just In Time) techniques to optimize manufacturing flow; maintaining the right mix and location of factories and warehouses to serve customer markets, and using location/allocation, vehicle routing analysis, dynamic programming and, of course, traditional logistics optimization to maximize the efficiency of the distribution side.
There is often confusion over the terms supply chain and logistics. It is now generally accepted that the term Logistics applies to activities within one company/organization involving distribution of product whereas the term supply chain also encompasses manufacturing and procurement and therefore has a much broader focus as it involves multiple enterprises, including suppliers, manufacturers and retailers, working together to meet a customer need for a product or service.
Supply Chain Risk Management (SCRM) is a discipline of Risk Management which attempts to identify potential disruptions to continued manufacturing production and thereby commercial financial exposure.
Supply chain security refers to efforts to enhance the security of the supply chain: the transport and logistics system for the world's cargo. It combines traditional practices of supply chain management with the security requirements of the system, which are driven by threats such as terrorism, piracy, and theft. Some analysts have raised concerns about supply chain security overreach. Typical supply chain security activities include:
* Credentialing of participants in the supply chain.
* Screening and validating of the contents of cargo being shipped.
* Advance notification of the contents to the destination country.
* Ensuring the security of cargo while in-transit via the use of locks and tamper-proof seals.
* Inspecting cargo on entry.

